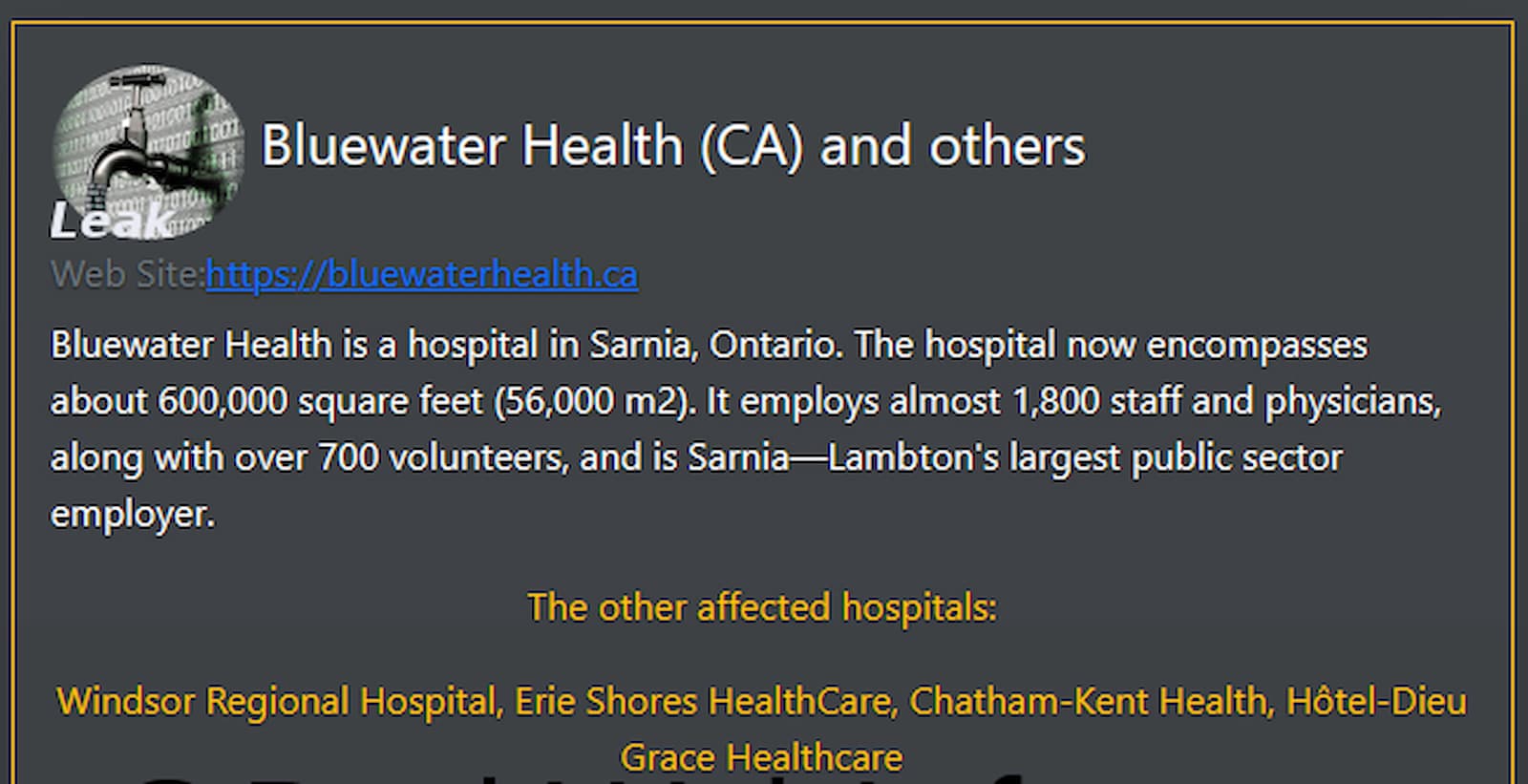
The division of cybersecurity professionals into teams brings clarity to their distinct roles. While terms like “offensive” and “defensive” could be used, it would be too broad of a distinction. For example, red teaming and pentesting are different things, but are both under the offensive umbrella.
Cybersecurity often draws parallels to war, where one team takes the offensive and the other defends. Historically, the color red has represented the aggressor, while the calming color blue symbolizes the defender. This analogy holds true in cybersecurity, where the red team launches attacks and the blue team defends. This standard terminology simplifies communication among cybersecurity experts and helps everyone understand their roles and objectives in various security assessments and exercises.
Red Team
The red team involves a group of experts simulating cyberattacks on an organization’s systems, networks, and applications. The primary goal of red teaming is to complete some type of objective which typically involves vulnerabilities and weaknesses in an organization’s defenses.

They act as attackers who use various tactics and techniques to breach security measures to complete the mission.
Red teaming is the art of adversary emulation, where they attempt to mirror attacks that malicious hackers would use. By doing so, red teams help organizations uncover vulnerabilities that might go unnoticed in routine security assessments.
The insights gained from red team exercises are highly valuable. They provide organizations with a realistic assessment of their security posture, helping them understand where they need to improve. Red teaming is not necessarily about fault-finding but rather about enhancing resilience by proactively addressing weaknesses.
Red teaming differs from pentesting by trying to remain incognito as they emulate real attacks. On the flip side, penetration testers attempt to find any and all vulnerabilities and report them. Penetration testing will typically last under a month, where the testers will then inform the company about findings and best practices.
In a typical red team engagement, the red team will use a combination of known attack methods, creative thinking, and the latest threat intelligence to test an organization’s defenses comprehensively. Ultimately, red teaming serves as an essential tool for organizations to stay ahead of cyber threats. It provides a practical way to continuously assess and improve their security measures, ensuring they are well-prepared to defend against real-world attacks.
Blue Team
The blue team also plays a pivotal role in an organization’s cybersecurity strategy. While the red team focuses on simulating cyberattacks, the blue team takes on the responsibility of defending against these simulated attacks.

The blue team is composed of cybersecurity experts who are tasked with protecting an organization’s systems, networks, and applications from the red team.
The primary goal of the blue team is to detect and respond to any security threats or incidents that may arise. They act as the first line of defense, constantly working to maintain and enhance the security posture. Unlike the red team, whose objective is to find and exploit a vulnerability, the blue team’s mission is to detect and protect against them.
The blue team proactively sets up security measures, including firewalls, intrusion detection systems, and endpoint security solutions to detect potential threats.
One of the blue team’s essential functions is to conduct incident response exercises. In the event of a security breach or cyberattack, they spring into action to mitigate the damage, investigate the incident, and implement corrective measures. Their effective response is critical in minimizing the impact of security incidents and preventing future breaches.
At the end, the blue team collaborates with the red team to share insights and knowledge gained from the exercises. This collaborative approach helps both teams continually refine their strategies and tactics, creating a stronger overall cybersecurity posture for the organization.
Collaboration
In the aftermath of a red team exercise, analysis and reporting is done. After a successful red teaming event, the red team doesn’t just conclude with their successful objective. Instead, they provide a report detailing their actions.
This report includes various critical elements including:
- A detailed account of the attack scenario.
- The techniques employed with evidence of their execution.
- A list of vulnerabilities exploited during the exercise.
- Risk assessments and mitigation strategies.
- Areas for technical improvements.
While the red and blue teams form the primary teams of cybersecurity, there are also secondary colors you may come across.

- Yellow teams build secure software.
- Green teams fix vulnerabilities based on defender findings.
- Orange teams fix vulnerabilities based on attacker findings.
- Purple teams are a collaboration between red and blue teams working on the same side.
Conclusion
These colorful teams – red, blue, green, orange, yellow, and purple – each bring their own unique role to the table. Most importantly, the red team emulates hackers, and the blue team tries to defend against the hackers. The secondary colors all provide distinct value and security analysis. Together, they create a well-rounded cybersecurity strategy that helps organizations stay secure in a complex digital landscape.