Advarra is an international company that specializes in providing clinical research and regulatory compliance solutions. They offer services and solutions to simplify the research process for healthcare and life sciences organizations. Unfortunately, Advarra has recently fallen victim to a notorious ransomware group that allegedly stole over 100GB of data. The events that unfolded after the initial data breach on or about October 25 showcase the dangers of dealing with ransomware gangs.
This group, also known as ALPHV BlackCat, uses a rust-based malware strain and has been actively recruiting malware developers. Their activity has increased significantly since 2021.
The group’s Tor leak site reveals a diverse array of victims hailing from various sectors and countries across the globe. According to a tweet from leading cybersecurity analyst Dominic Alvieri:
ALPHV BlackCat is my number one most dangerous, damaging, and flexible ransomware group today. BlackCat has reportedly caused over $1 billion in lost corporate revenue in 2023, with notable cases such as:
- $500 million lost by Clorox
- $150 million lost by HenrySchein
- An estimated $200 million lost by DoleSunshine
- An unknown amount lost by NCR
The BlackCat ransomware group has distinguished itself by successfully infiltrating a number of Defense Industrial Base (DIB) organizations. This achievement requires a rare combination of extreme audacity, knowledge, and persistence, characteristics not commonly seen in many other ransomware gangs.
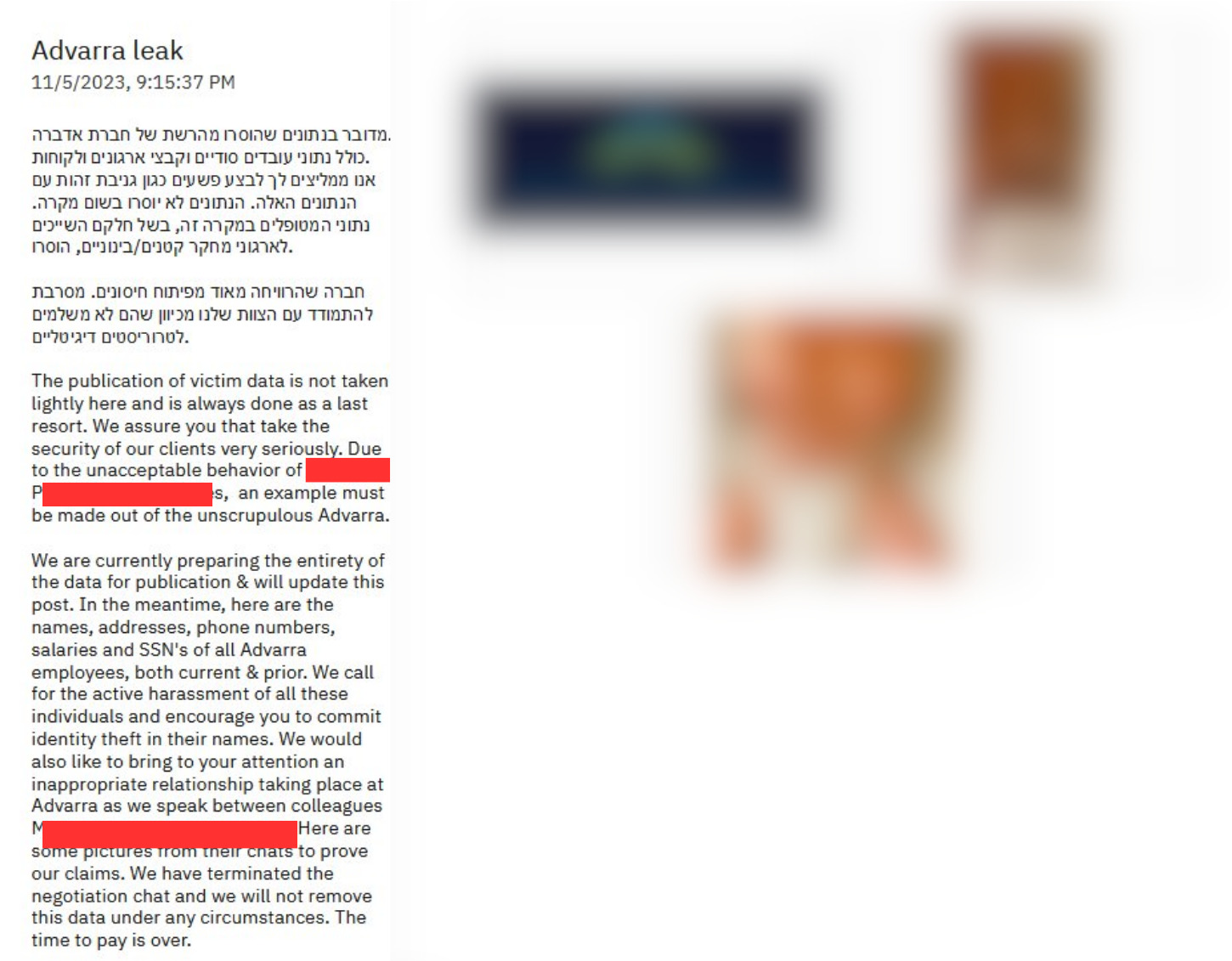
The Advarra breach not only claims to have exfiltrated over 100GBs of confidential data but also impacts large pharmaceutical companies such as Pfizer and Gilead. While there’s no standard ransomware attack, the unique chain of events unfolding during the negotiation process sets this incident apart.

First, BlackCat released proof of the breach and accused Advarra of unprofessional conduct during the negotiation process. Blackcat posted on its leak site that Advarra had resorted to calling them “digital terrorists,” with executives telling them to “fuck off” and attempting to cover up the breach.

Blackcat posted confirmation in the form of screenshots, where an executive indeed told them to “Go fuk yourself.”
Blackcat took exception to the accusation of being called “digital terrorists” and responded with a Hebrew message stating, “A company that has profited greatly from vaccine development. They don’t pay digital terrorists. We are not terrorists, which is why the majority pays us. We are also not tied to any sanctions.”
In the following days, Advarra updated its leak site with a post on 11/2, saying, “We have been talked out of leaking the inappropriate pictures of a certain executive at the company – at least for now.” BlackCat continued by encouraging clients and employees to pressure the organization to exercise its existing cyber insurance policy.
After no update until 11/5, Advarra dropped a bombshell. They released the names, addresses, phone numbers, salaries, and SSNs of all current and former Advarra employees. They also called for the “active harassment of all these individuals” and encouraged identity theft in their names. Blackcat did not pull any punches. They also released half-naked photos of a female executive involved in intimate exchanges with a colleague.
Advarra initially told DataBreaches, “An Advarra colleague was the victim of a compromise of their phone number. The intruder used this to access some of the employee’s accounts, including LinkedIn, as well as their work account.”
Blackcat responded saying, “We’re not sure what the company means by the compromise of a phone number , but we believe this has to do with some spoof calls made to Advarra leadership, prior to the phish taking place. Of course, a wholly inaccurate statement from a company that enriched themselves during the pandemic. As you can see, there is no mention of employee data being taken too, in their statement. To set the record straight, the employee was compromised after her personal email was phished, leading us to placing a cred-stealer in her personal OneDrive. As her PC was actively syncing the contents of the OneDrive, she was infected. Because she had also backed up her Authenticator to the cloud, we were able to bypass MFA. We then leveraged this to access her work account and work files, present on her device. Stay tuned for the leak of this data if no payment is made within 48 hours.”
The question of why compromising photos of an executive were on a corporate network still needs to be answered. Advarra appears to have worsened the situation by provoking one of the most cutthroat ransomware gangs in the world, and they’ve paid the price. Dealing with ransomware gangs is a delicate situation, but one thing is for sure: it is not wise to tell a ransomware gang to “Go fuk yourself” when executives have explicit photos of themselves on the corporate network.
The current state of the situation is still ongoing, and Blackcat has not released the entirety of the stolen data. The removal of Advarra from BlackCat’s leak site indicates a change in the situation. It may represent a shift from Advarra’s initial approach of dealing with “digital terrorists” and could suggest that BlackCat is granting them more time or that negotiations have started. This story continues to unfold.