In a coordinated international effort, the FBI, Europol, and various agencies worked together to dismantle the notorious malware group Ragnar Locker. This group, named after the ransomware strain they created, emerged in 2020 and swiftly gained notoriety for their suspected involvement in attacks against 168 international companies. The sting proved to be a critical blow to the ransomware gang; It managed to take down nine servers in three different countries, conduct home searches and interviews with six suspects, and apprehend the “main perpetrator,” believed to be a key developer within the Ragnar group.
The Ragnar Locker malware is a potent threat targeting both Windows and Linux systems. Its strategy involves infiltrating a victim’s machine, exfiltrating their files, encrypting them, and then demanding a ransom. Notably, when a device falls prey to this ransomware, only the critical system files remain unchanged, allowing the computer to function, but all other files become encrypted. To add an extra layer of damage, volume shadow copies, which help you recover files, are targeted and deleted. So, RangarLocker not only steals data from the victim’s system but also encrypts their files, making them unusable. This technique, known as “double extortion,” is a hallmark of the Ragnar Locker group. It compels victims to make two payments: one to decrypt their files and a second to prevent the release of their data.
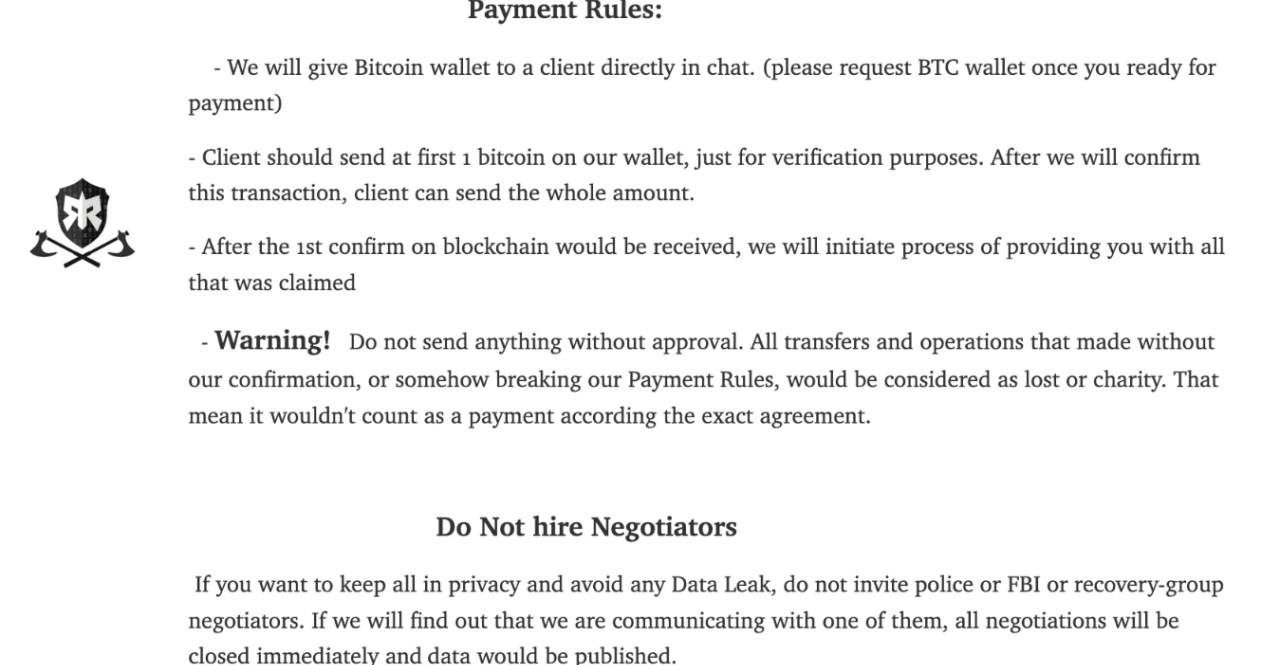
Ragnar Locker’s preferred currency for their extortion demands is Bitcoin. They offer a unique “service” to their victims – in exchange for the ransom payment, they provide insights into how they breached the victim’s system and how to prevent future breaches. They also promise to eliminate all system backdoors, with the sole condition being that victims avoid contact with law enforcement or professional negotiators. If Ragnar Locker suspects that authorities are closing in, they will release the stolen data. The group runs a data leak site called the “Wall of Shame” on the Tor network. Hosting a website on the Tor network ensures anonymity by routing traffic through a decentralized network of volunteer-operated nodes, making it difficult for anyone to trace the site’s physical location or the identity of its operator.
If victims fail to cooperate, Ragnar Locker resorts to intimidation tactics by releasing snippets of the stolen information as threats, escalating these tactics until they ultimately expose all the compromised data, should their timeframes not be met. Over the past three years, Ragnar Locker has allegedly collected tens of millions of USD in ransom payments, demanding between 5 and 70 million in cryptocurrencies from their victims. Their targets span various industries, including travel, aerospace, media, and medical.
The international crackdown on Ragnar Locker began in October 2021 with investigators sent to Ukraine. This operation led to the arrest of two prominent Ragnar Locker operators. Yet, the threat persisted, prompting the FBI to release a flash alert in March 2022, revealing that 50 organizations across critical infrastructure sectors had fallen victim to Ragnar Locker ransomware.
In the latest strike against the group, which unfolded between October 16 and 20, authorities placed five suspects under investigation and arrested the main perpetrator. A 35-year-old man from Paris, suspected to be the primary developer, was apprehended and his associates interviewed. This operation also resulted in the seizure of nine servers, dismantling Ragnar Locker’s dark web leak site. Among the confiscated evidence were laptops, mobile phones, and various cryptocurrencies of unknown amounts. With links to Russia, the Ragnar Locker group had established a presence across European infrastructure, prompting searches in Czechia, Spain, Latvia, the Netherlands, Germany, and Sweden.
While this may not be the final blow to eradicate Ragnar Locker from the digital landscape, it is undoubtedly a significant step in the right direction. Seizing their core infrastructure and apprehending a key programmer is a considerable achievement. Ragnar Locker, though not the largest cybercriminal gang, needed to be neutralized due to its propensity for targeting critical infrastructure.
The group’s longevity and continued pursuit of such high-stakes targets made them a priority for cybersecurity and intelligence agencies across the globe. The participating countries in this multifaceted operation were the Czech Republic, France, Germany, Italy, Japan, Latvia, the Netherlands, Sweden, Spain, Ukraine, and the USA.