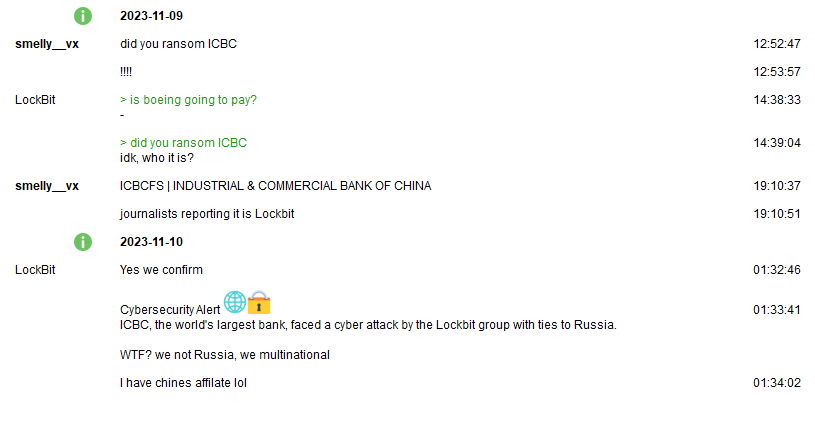
The Global Research and Analysis Team (GReAT) at Kaspersky reports on Advanced Persistent Threats (APTs) on a quarterly basis. In the Kaspersky Q3 APT report, several noteworthy threats have come to the forefront. This article will explore a recent secure USB attack, a cyber espionage group from South America, a newly identified Russian APT, an in-memory implant, and the latest activities of a North Korean hacking group.
New Wave of Advanced USB Drive Attacks
In the third quarter, a highly sophisticated cyberattack was uncovered, in which cybercriminals used compromised secure USB drives to infiltrate government systems. This attack, coined “TetrisPhantom”, is highly targeted and directed toward Asian countries that employ a specific type of secure USB drive. While the attackers remain unidentified, it’s not uncommon for Chinese APT groups to use USB drives to distribute malware.
What makes this attack stand out is the utilization of a particular type of secure USB drive. Secure USBs are safer than regular USBs because they have encrypted and password-protected partitions, providing an additional security layer. Kaspersky, in their analysis, revealed the intricacy of the attack, involving “virtualization-based software obfuscation for malware components, low-level communication with the USB drive using direct SCSI commands, self-replication through connected secure USB drives to propagate to other air-gapped systems and injection of code into a legitimate access management program on the USB drive which acts as a loader for the malware on a new machine.”
BlindEagle’s Unique Espionage Techniques
BlindEagle, a cyber espionage group operating in South America, has garnered attention for its unconventional methods. They have been deploying Remote Access Trojans (RATs) to compromise victim’s computers and networks. RATs provide unauthorized access to manipulate files, steal data, and even take control of the victim’s system from a remote location. The attackers use open-source RATs and phishing emails that resemble those from government agencies to deliver the RATs.
BlindEagle’s success in targeting organizations in lesser-reported regions demonstrates the vulnerability of less-prepared organizations to relatively simple attacks.
The Emergence of “BadRory”
In late 2022, a new Russian-speaking APT group, “BadRory,” emerged. This group targets a broad range of entities, including government organizations, military contractors, universities, and hospitals. Their attacks involve spear-phishing emails that initiate a multi-level infection scheme, culminating in the installation of a new trojan.
Once installed, this trojan exfiltrates files and gains control of the victim’s machine
The attacks carried out by BadRory are widespread within Russia, but the group remains unknown.
Advancements in “TargetPlug” Malware
In January, an in-memory implant known as “TargetPlug” was identified, particularly affecting the gaming sector in South Korea. A second wave of this malware surfaced in April, expanding its target list to include entities in the software and entertainment industries across Spain and Mexico.
The latest variant of “TargetPlug” is the most advanced yet, with architects removing telltale signs of its presence and introducing a string hashing algorithm for added evasion.
This hashing algorithm obscures text-based components of the malware, making it challenging for security tools to detect and analyze the malware’s patterns.
Lazarus Group’s Ongoing Disruption
The Lazarus Group, a government-backed hacking team from North Korea, has been responsible for numerous disruptive acts over the years. This group remains highly active, recently deploying two new Remote Access Trojans (RATs) known as “QuiteRat” and “CollectionRat.”
In their most recent activities, Lazarus has targeted the defense industry and nuclear engineers. They post fake job interviews to mislead victims into opening malicious applications.
“To avoid detection by behavior-based security solutions, this backdoored application operates discreetly, only activating when the user selects a server from the drop-down menu of the Trojanized VNC client. The application launches additional payloads into memory and retrieves further malicious code.”
This malware primarily aims to exfiltrate files to a remote server. To avoid detection by security systems that rely on behavior analysis, Lazarus has engineered the malware to turn off behavior monitoring by manipulating user-mode syscalls.
Conclusion
The latest report released by Kaspersky underscores the significance of cybersecurity vigilance in the face of emerging APTs.